Why is DNS security critical?
From a network security perspective, Domain Name System is one of the most widely used network protocols across the Internet.DNS is an open protocol used in 99% of internet connection. Unfortunately, it is packaged into a UDP 53 packet with plain text naturally. The open nature has made DNS become a leading pathway for ransomware and other security risks.Now, the new DNS privacy standard is DNS over TLS, DoT. TLS, Transport Layer Security, helps the new standard to address what is the ‘last mile’ problem for DNS security. The communication between DNS client, your local DNS server or your PC, and your DNS provider, mostly would be Google, are almost always unencrypted and, therefore, subject to hijacking and other threats. DoT not only strengthens the DNS security by encrypting but also authenticating the DNS server with a digital signature.The usual way of blocking threat is to use enterprise threat protecting mechanism against every daily threat. The most effective way to improve your security stack is to protect your network at the start point.
Trade-offs of using DoT
In the real case, the new DNS protocol makes it more difficult to be used for immoral purposes. But, it will make it challenging to get the internal security mechanism to work as well. However, enterprises always want to maintain internal security control over their DNS server. For those use cases, the new protocols come with notable security trade-offs
- Bypassing enterprise controls: Although DoT provides the solution to gain the DNS level security by encrypting the DNS requests and response, it might unconsciously bypass enterprise contents control.
- DNS server performance reduction: traditional DNS depends on UDP, User Datagram Protocol, and it is unreliable but more efficient. DNS over TLS will run over the TCP, Transmission Control Protocol, which needs more resources on your local DNS server. Apart from that, using TLS requires your DNS server to encrypt queries and decrypt responses, and the size of DNS packets will also increase accordingly. Adding more resources needs to be put into consideration if the same performance is required.
- Education for end-users: DoT is in constant development, bringing challenges to the existing infrastructure. All managers and architects, whether they are running infrastructures on public cloud or private networks, should be aware of the evolution.
Best Practice
- Choosing a reliable DNS provider, who will guarantee 100% uptime and using technology like anycast to perform resiliently.
- Starting Looking after your security concern. Your DNS server should proactively respond to threats. You should be able to use the Internet’s infrastructure to block malicious and unwanted domains, IP addresses, and cloud applications before a connection is ever established.
- Blocking direct DNS requests is a good place to start. Between the internal users and DNS providers on the Internet, there should be another step in the middle, like local DNS infrastructure. It would allow the administrator to comprehensively apply DNS policy without getting end-users involved.
- Making sure all queries are accountable. Your administrator is capable of seeing logs for all DNS activity to simplify investigation. The logs will also be the reference for security decisions.
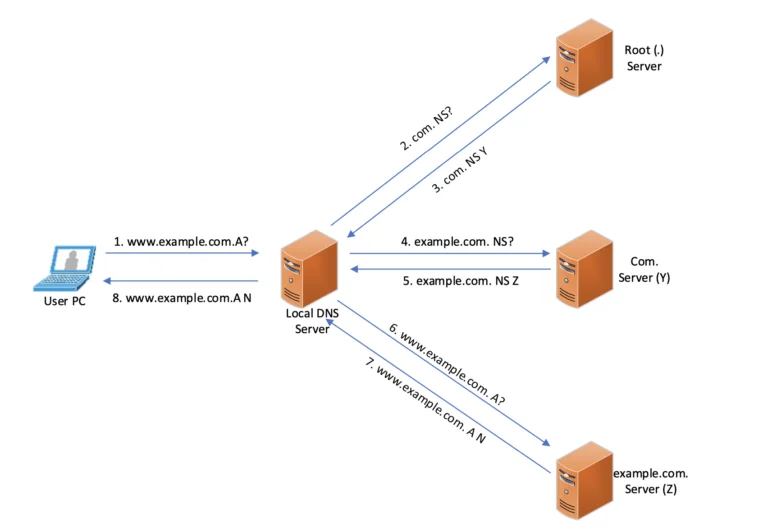
Traditional Way of DNS Resolution
DNS Resolution Process with Secured DNS Provider
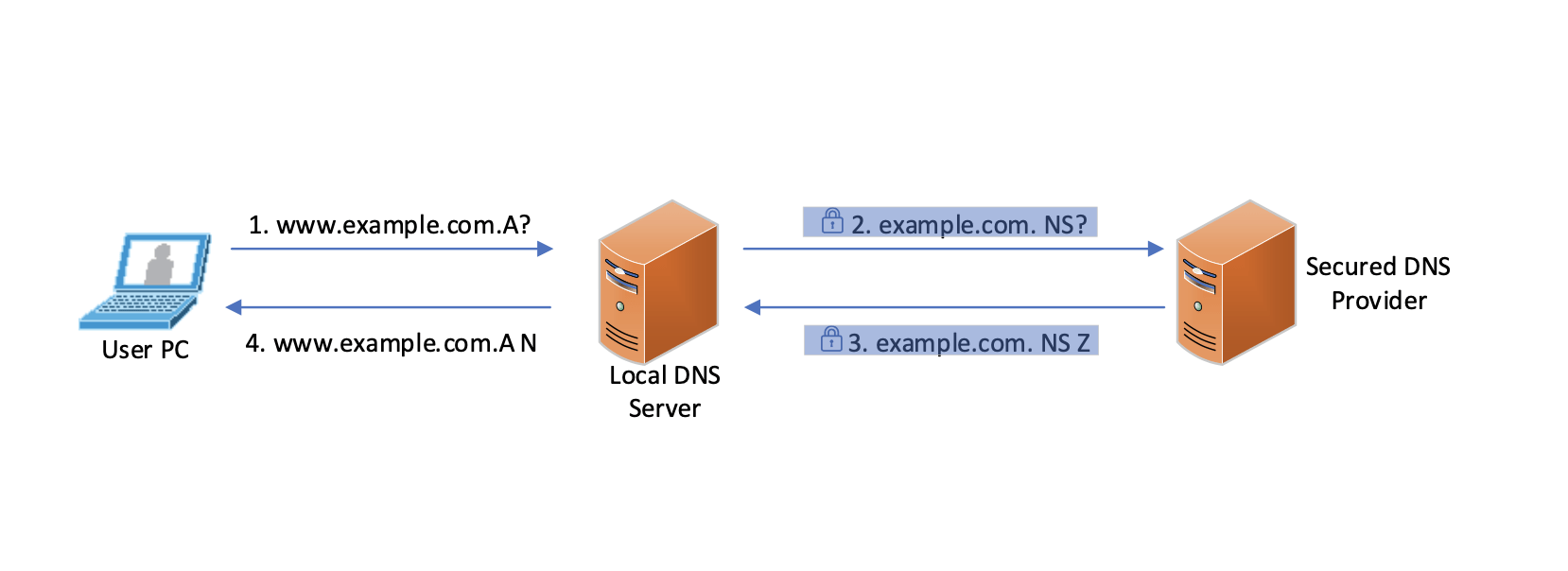
More details on DNS security privacy and DNS security provider are available in the Managed DNS security solution. Stop blindly trust every websites without, start using Advanced Threat Intelligence to secure your DNS infrastructure.
More security solutions are available on Managed Service Center. Start looking after your network security with right partner.
If you’re interested to learn how more about DNS Security, contact us today at info@sprintnetworks.com

