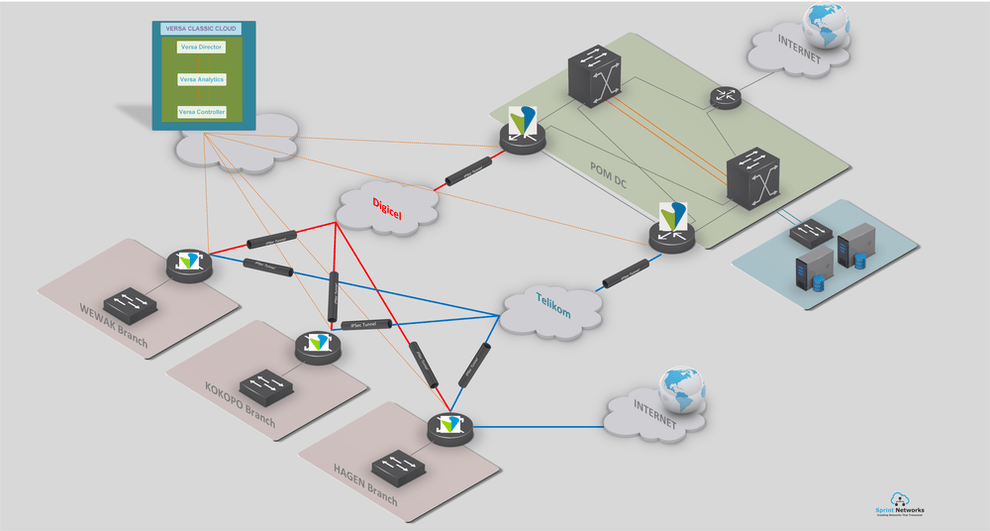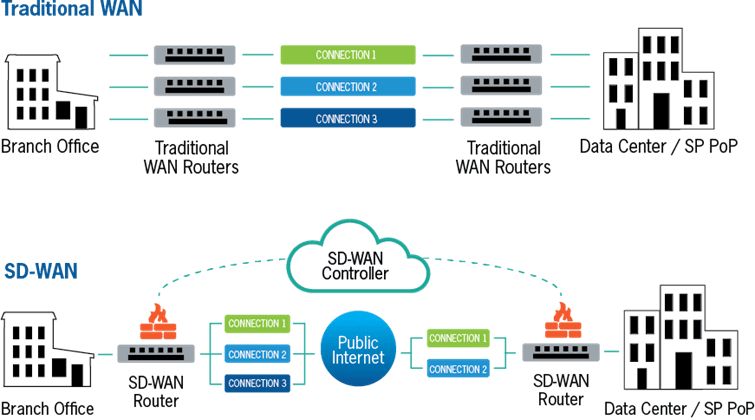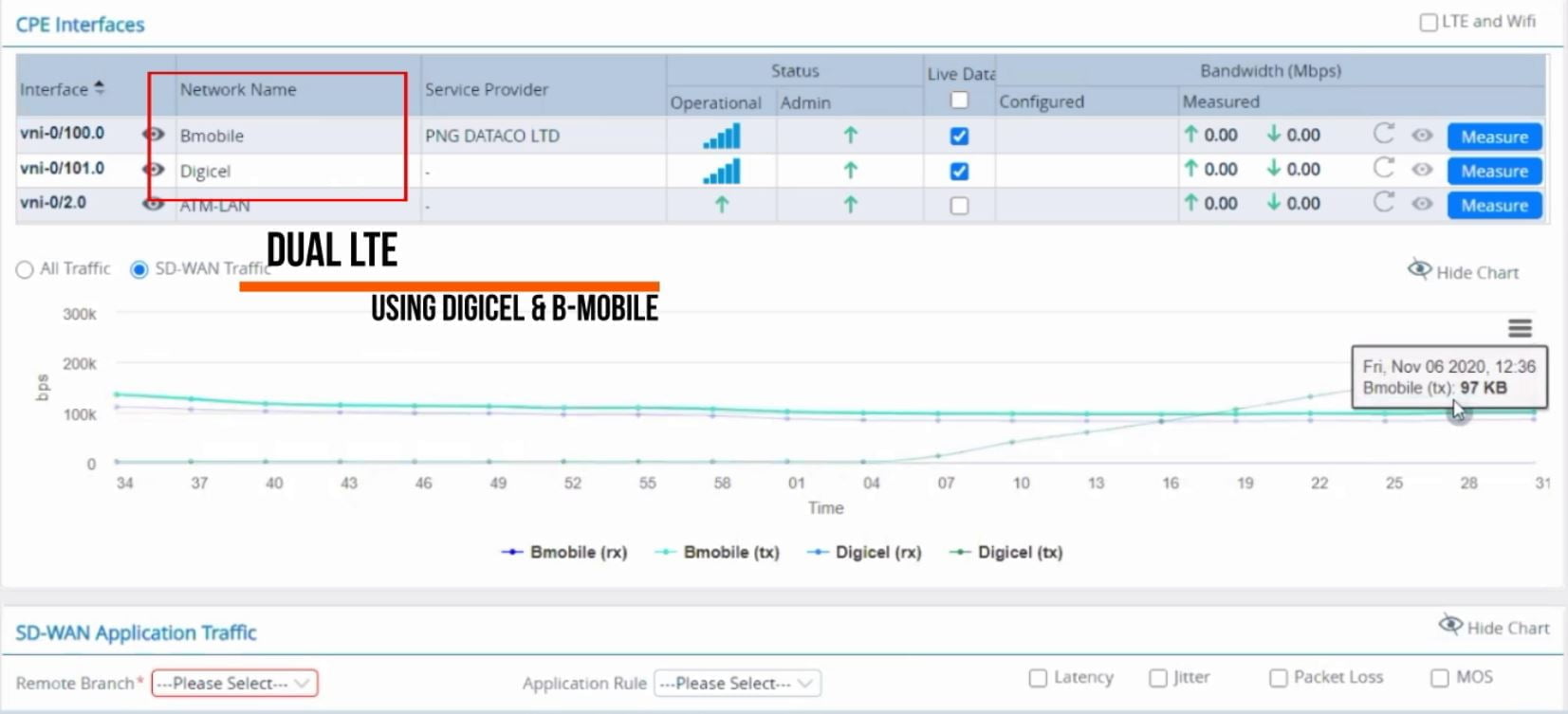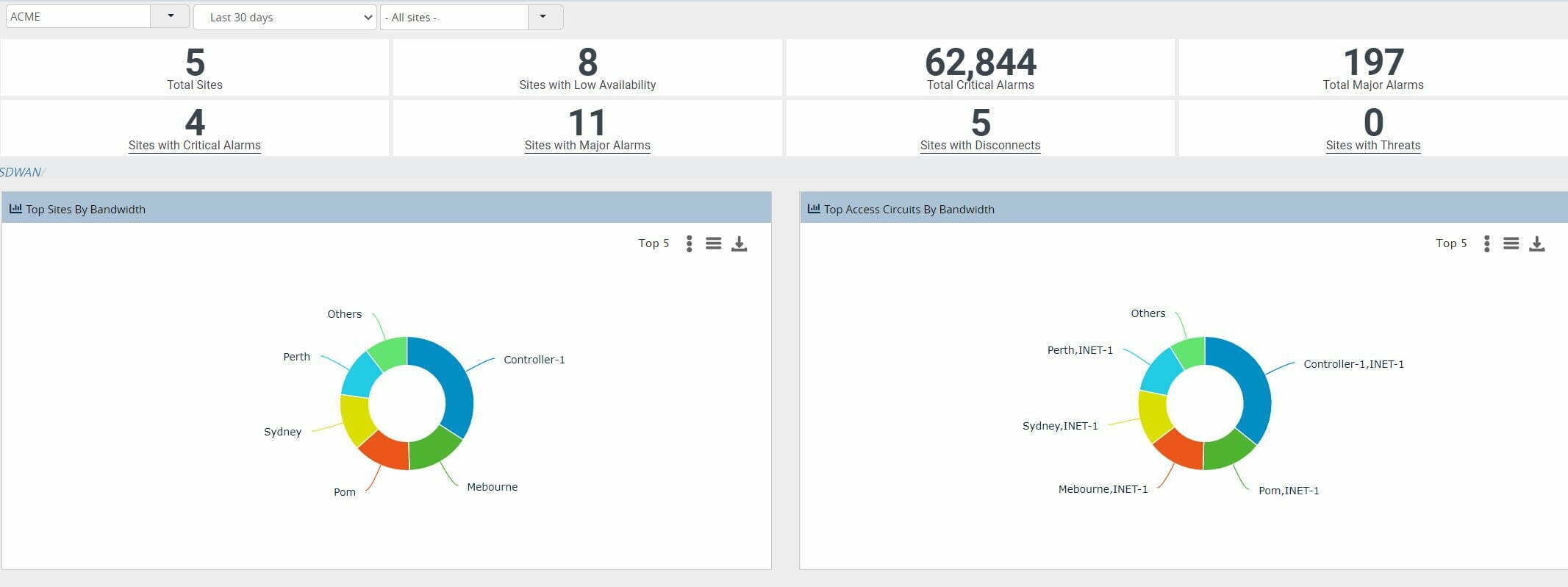
The last year has seen a fundamental shift in the way many companies operate, with staff rapidly moving out of the office and into their homes to continue working remotely. This shift to perimeter-less working has forced IT departments and Security teams to focus on how they manage the devices those staff are using, since they’re no longer connected directly to the office network.
The principle of perimeter-less working focuses on protecting the resource, rather than the network or infrastructure of a company. This comes in many forms, such as encrypting data both in transit and at rest, using multifactor authentication to prove user identities, and restricting which users and devices can access company resources.
Throughout this, Endpoint Protection remains a key tool in the Security Team’s arsenal; hackers may be using phishing as the initial attack vector, but placing malware, ransomware or other malicious code onto the user’s device is still a popular means to gain access to a company’s crown jewels.
While there are many endpoint protection products available on the market, we’re going to focus on two general approaches and explore how they can help protect your users.
DNS Filtering
DNS is the cornerstone of modern Internet communications and is used by both genuine websites and the malicious parts of an attacker’s infrastructure. The basics of DNS have remained largely unchanged for decades now – a user simply types a friendly name such as google.com into their browser, and DNS looks up the underlying server IP address for you.
The danger is that public DNS servers are usually unaware of the content or nature of the site they’re looking up. Many lookups also occur behind the scenes of your computer and users aren’t aware they’re even happening. This allows attackers to build sites on the Internet that can be used as part of an attack, for example running a phishing site or hosting malicious code that can be called from a victim’s machine.
Cloud-based DNS filtering by services such as Cisco Umbrella enable you to identify, categorise and filter traffic based on those DNS lookups, stopping attackers in their tracks and blocking access to unwanted or malicious websites.
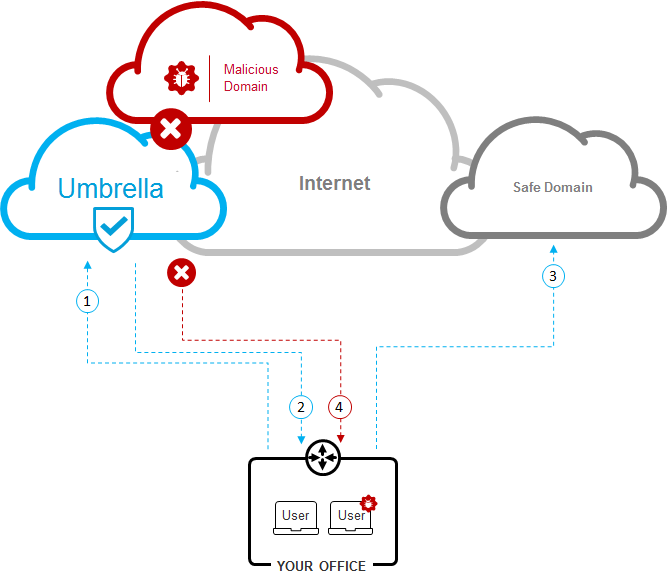
Cisco Umbrella DNS Protection
Anti-Virus Protection Applications
A more traditional approach to endpoint protection comes in the form of anti malware applications. These have grown up substantially since the early days of anti-virus, and now come with a wide array of capabilities beyond simple signature-based detection.
These tools still include the traditional approach of blocking executables, macros and scripts, but also reach into advanced behavioural analysis using centrally managed Machine Learning to monitor what is happening across the system and intercept suspicious activities.
Tools such as the Fortigate FortiClient include automatic sandboxing, exploit prevention and memory protection, and monitor the machine for vulnerabilities and configuration control to ensure compliance.
When used in conjunction with a DNS-based service, these tools can provide a “best of both worlds” approach to security, blocking access to malicious sites and detecting and protecting against anything malicious that sneaks through. This will protect your endpoint as well as your company network while working remotely.