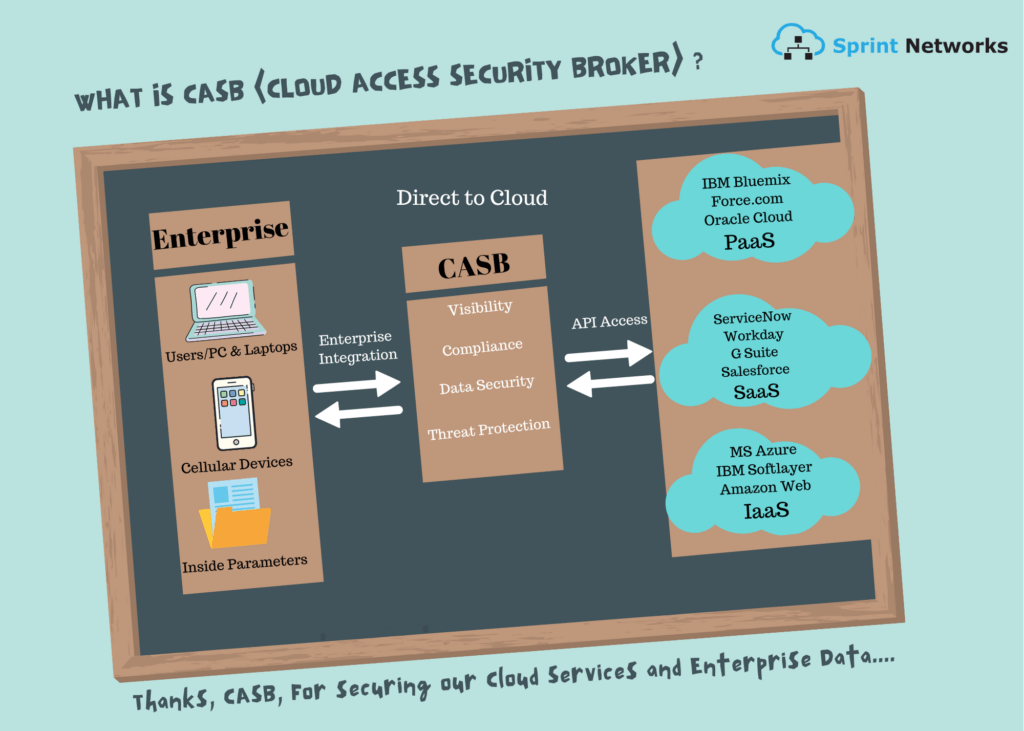
CASB
CASB Is an on-premises or cloud based software that sits between cloud service users and cloud applications, and monitors all activity and enforces security policies. A CASB can offer a variety of services such as monitoring user activity, warning administrators about potentially hazardous actions, enforcing security policy compliance, and automatically preventing malware. CASB sales have soared as cloud security concerns have grown, especially the use of “Shadow IT” cloud services that IT security teams don’t know about.
Four foundation of CASB architecture
- Visibility
CASB gives enterprises visibility over user activity in the cloud. Cloud applications that are off site and prone to governance risk, compliance processes of the organization. The visibility features that CASB offers allows controllers to view who uses which cloud app, departments, geo-locations and devices affiliated to the users.
- Compliance
CASB enforces Data loss prevention policies at a granular level to meet compliance requirements. It helps in identifying sensitive data in the cloud that might be vulnerable and of high risk.
- Data Security
Data security features such as encryption, tokenization, access control including information rights management is governed by CASB.
- Threat Protection
CASB’s layout as a middle man helps detect and respond to malicious threats, privileged user threats and compromised accounts.
Why do we require CASB?
With enrollment of various cloud features and service technology, end point users are facing hardships maintaining database integrity in cloud. Even for an enterprise when it comes to cloud computing they are not aware of the human errors, data leaks they might be facing onsite even before the data path is created for an offsite transmission.
CASB has multiple use-cases for the enterprise:
- Secure Shadow IT
Shadow IT is the unauthorized use of cloud services by line of business staff. IT teams are usually not aware of the Shadow IT. It has no governing policies, is not subject to corporate security and compliance. This exposes the enterprise to a huge deal of security risks.
A recent survey by Intel security shows that more than 2000 IT personnel, 40 percent of cloud services are running without the involvement of IT. The result of which, IT professionals think that shadow IT is interfering with their ability to keep cloud services secure. Majority of the respondents have said that malware has been tracked from those cloud applications.
- Govern Device Usage
CASB can simultaneously monitor and control user activities as the users are browsing cloud services from endpoint devices, app or client. It helps identify device ownership class, privileged accounts and prevents unauthorized activities in the cloud.
- Secure Data
CASBs can prevent data exfiltration from an approved to an unsanctioned cloud service, enforce separate policies for personal and corporate instances of the same cloud service, enforce a policy at the activity or data level across a group of services, enforce conditional activity-level policies, enforce layered policies, and apply encryption when it comes to data protection.
- Block Malware
CASB can provide an enterprise protection against threats, shield and remediate malware in a sanctioned cloud service to and from a unsanctioned cloud service. It also alerts the enterprise about login anomalies, excessive downloads, uploads and prevents data infiltration involving new employees.
Where does CASB run?
CASB is found in both onsite premises and offsite in the cloud. But logically it sits between the user and the cloud acting as the middle man. Considering the physical location, a CASB has to be in either of the two places i.e. in a corporate data center or in the cloud itself. It depends on the user choice and as to what sort of network deployment they prefer. CASB can be used as a SaaS or hosted on a physical or virtual appliance.
How does CASB function?
CASB mainly operates in 2 ways. It can either be set up as a proxy i.e. Forward proxy or a Reverse proxy – or it can function in API mode using the cloud service providers APIs to maintain cloud access and apply security policies. Increasingly CASBs are becoming “mixed mode” or “multi-mode”.
Forward Proxy
All types of cloud applications can use forward proxy. All the data passes through forward proxy, but a requirement to that is the installations of self-signed certificates on every single device that accesses the proxy. In a large corporate organization, it can be difficult to deploy because of the distributed environment they might have. One with a large number of employees and owned mobile devices.
Reverse Proxy
A reverse method is much easier because it is accessible from any device, anywhere, without the need for special configuration or certificate installation. The backside to reverse proxy is that it can’t work with a client-server type application, which have hard coded hostnames.
API-Based Systems
API based systems are easy to be deployed in comparison to the other two. The drawback to this is that the range of cloud applications they can work fully is limited as not all applications can provide API support.
“Proxy or API architectures from CASB have different abilities to perform different actions, which have various implications for how that provider delivers the four pillars for a specific cloud service,” Gartner says.
In over the few years. Gartner expects many cloud service providers to have their own API.
One CASB may not be enough
The various capabilities of CASBs- forward proxy, reverse proxy, API based or multimode vary. CASB differs from each other as the development of each might differ at the mercy of the vendors who have developed it. Just because a CASB supports one application doesn’t mean it might support as much or to the extent of another CASB.
Choosing a CASB that supports the application an enterprise uses now, and are likely to use in the future might be a challenge. Mostly office apps like CRM, HR and ERP are generally well supported but industry specific apps e.g., healthcare industry might not be.
One of the advices handed out by Gartner is that,” be cautious when entering into long-term contracts. Build in flexibility as you may require more than one CASB or may need to change from a current provider to the one that supports your enterprise use case thoroughly.
CASB Market size
The CASB market size has grown by a significant number as the demands for cloud security and middle man data security rises. The CASB market is expected to grow from $3.4 billion in 2015 to $7.5 billion in 2020, with a compound growth rate of 17.6%.
The increasing adoption of cloud-based applications such as Office 365, Salesforce, Google Apps is a playing a major role in fueling the growth of CASB market.
More than dozens of CASB startups have been launched since 2010 and a number of major CASB vendors have been acquired by bigger players in IT security.
Major CASB vendors include:
· Bitglass
· Blue Coat (owned by Symantec)
· CipherCloud
· CloudLock (owned by Cisco)
· Forcepoint (through Skyfence acquisition; owned by Raytheon)
· Microsoft (through Adallom acquisition)
· Netskope
· Skyhigh Networks (acquired by McAfee)
